The Security Risk Assessment Tool is not intended to be an exhaustive or definitive source on safeguarding health information from privacy and security risks. Probability is something a risk event will occur whereas impact is the significance of the consequences of a risk event. Monitor your business for data breaches and protect your customers' trust. The risk assessment survey refers to begin documenting the specific risks or threats within each department. The two main approaches to risk analysis are qualitative and quantitative. References and additional guidance are given along the way. Could we recreate this information from scratch? While hackers, malware, and other IT security risks leap to mind, there are many other threats: Some common threats that affect every organization include: After you've identified the threats facing your organization, you'll need to assess their impact. Test the security of your website, CLICK HERE to receive your instant security score now! 0000005019 00000 n
IT Governance provides a range of risk assessment and cybersecurity products and services to suit all needs. A risk estimation and evaluation is usually performed, followed by the selection of controls to treat the identified risks. 0000004100 00000 n
You may also leave a message with our Help Desk by contacting734-302-4717. Do you have the Organisations are increasingly taking the initiative when it comes to firming up their supply chain security. What is risk management and why is it important? Download Version 3.3 of the SRA Tool for Windows [.msi - 70.3 MB]. What are our organization's most important information technology assets? There are many questions you can ask to determine value: The first step is to identify assets to evaluate and determine the scope of the assessment. The objectives of performing quantitative risk analysis process provide a numerical estimate of the overall effect of risk on the project objectives. identify, rate and compare the overall impact of risks to the organization, in terms of both financial and organizational impacts; enhance communication and decision-making processes as they relate to information security; increase employee awareness about security measures and risks by highlighting best practices during the risk analysis process; and. Cyber risks are sometimes referred to as security threats. The primary goal of this step is to implement the measures to remove or reduce the analyses risks.
0000000016 00000 n
Please leave any questions, comments, or feedback about the SRA Tool using ourHealth IT Feedback Form. The assessing individual risk evaluates the probability that each risk will occur and effect on the project objectives. Once the standard is formally incorporated into the organization's information risk management policy, use it to classify each asset as critical, major or minor.
However, if you have good IT staff who can identify vulnerabilities and they update the operating system to version 1.8, your vulnerability is low, even though the information value is still high because the backdoor was patched in version 1.8. A few things to keep in mind is there are very few things with zero risk to a business process or information system, and risk implies uncertainty. It's not just whether you might face one of these events at some point, but what it's potential for success could be. This version of the SRA Tool takes the same content from the Windows desktop application and presents it in a familiar spreadsheet format. 0000005534 00000 n
As you work through this process, you'll understand what infrastructure your company operates, what your most valuable data is, and how you can better operate and secure your business. Arguably justifying a $1 million budget each year to be prevented. Could our staff work without it? The impact of risks is often categorized into three levels: low, medium or high. Remember, not all assets have the same value. Risk analysis is the process of identifying and analyzing potential issues that could negatively impact key business initiatives or projects. Download the SRA Tool User Guide for FAQs and details on how to install and use the SRA Tool application and SRA Tool Excel Workbook. Learn how you, as an executive, can manage cyber risk across your organization. Most organizations include asset value, legal standing and business importance. The risk analysis is applied to information technology, projects, security issues and any other event where risks may be analysed based on a quantitative and qualitative basis. Can You Protect Patients' Health Information When Using a Public Wi-Fi Network? 0000006922 00000 n
IT Governance specialises in IT governance, risk management and compliance solutions, with a special focus on cyber resilience, data protection, the GDPR, the Payment Card Industry Data Security Standard (PCI DSS), ISO 27001 and cybersecurity.
Some features and formatting may only work in Excel. Most commonly, cyber risks are associated with events that could result in a data breach. trailer
Do Not Sell My Personal Info. Risk management process: What are the 5 steps? Thank You, Check your inbox for your welcome email! Enterprises and other organizations use risk analysis to: Organizations must understand the risks associated with the use of their information systems to effectively and efficiently protect their information assets. HHS does not collect, view, store, or transmit any information entered into the SRA Tool.  0000006337 00000 n
What is Double Extortion Ransomware? If your office has no physical security, your risk would be high. Use risk level as a basis and determine actions for senior management or other responsible individuals to mitigate the risk. Risk assessment the process of identifying, analyzing, and evaluating risk is the only way to ensure that thecybersecuritycontrols you choose are appropriate to the risks your organization faces. The Excel Workbook contains conditional formatting and formulas to calculate and help identify risk in a similar fashion to the SRA Tool application. Would losing this information have an impact on revenue or profitability? Date 9/30/2023. Cyber risks are categorized from zero, low, medium, to high-risks. Resulting in an estimated loss of $50m every 50 years or in annual terms, $1 million every year. They also provide an executive summary to help executives and directors make informed decisions about security.
0000006337 00000 n
What is Double Extortion Ransomware? If your office has no physical security, your risk would be high. Use risk level as a basis and determine actions for senior management or other responsible individuals to mitigate the risk. Risk assessment the process of identifying, analyzing, and evaluating risk is the only way to ensure that thecybersecuritycontrols you choose are appropriate to the risks your organization faces. The Excel Workbook contains conditional formatting and formulas to calculate and help identify risk in a similar fashion to the SRA Tool application. Would losing this information have an impact on revenue or profitability? Date 9/30/2023. Cyber risks are categorized from zero, low, medium, to high-risks. Resulting in an estimated loss of $50m every 50 years or in annual terms, $1 million every year. They also provide an executive summary to help executives and directors make informed decisions about security. 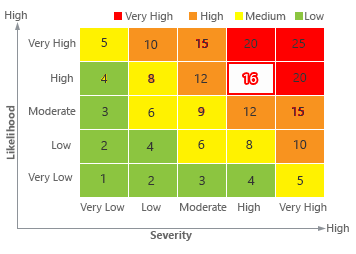 identify the impact of and prepare for changes in the enterprise environment, including the likelihood of new competitors entering the market or changes to government regulatory policy. Enterprise and organization used risk analysis: Every organization needs to understand about the risks associated with their information systems to effectively and efficiently protect their IT assets.
identify the impact of and prepare for changes in the enterprise environment, including the likelihood of new competitors entering the market or changes to government regulatory policy. Enterprise and organization used risk analysis: Every organization needs to understand about the risks associated with their information systems to effectively and efficiently protect their IT assets.
How UpGuard helps financial services companies secure customer data. A vulnerability is a weakness that a threat can exploit to breach security, harm your organization, or steal sensitive data. What are the internal and external vulnerabilities? The essential number of distinct approaches related to risk analysis are: JavaTpoint offers too many high quality services. Cyber risk assessments are defined by NIST as risk assessments are used to identify, estimate, and prioritize risk to organizational operations, organizational assets, individuals, other organizations, and the Nation, resulting from the operation and use of information systems. 0000009207 00000 n
If something is guaranteed to happen, it's not a risk. Quantitative analysis is not mandatory, especially for smaller projects. Am I reducing the risk in the most cost-effective way? Depending on the type and extent of the risk analysis, organizations can use the results to help: Done well, risk analysis is an important tool for managing costs associated with risks, as well as for aiding an organization's decision-making process. Internal or customer-facing systems need to be available and functioning for staff and customers to do their jobs. A cybersecurity risk assessment identifies the various information assets that could be affected by a cyber attack (such as hardware, systems, laptops, customer data, and intellectual property), and then identifies the various risks that could affect those assets. If your business isn't concerned about cybersecurity, it's only a matter of time before you're an attack victim. 0000004371 00000 n
Without expert guidance, this can only be worked out through trial and error. understand the financial impacts of potential security risks. ONC held 3 webinars with a training session and overview of the Security Risk Assessment (SRA) Tool. The three factors that impact vulnerability assessments are: Using this simple methodology, a high-level calculation of cyber risk in an IT infrastructure can be developed:Cyber risk = Threat x Vulnerability x Information Value. Analyze controls that are in place to minimize or eliminate the probability of a threat or vulnerability. The analysis of risk should be occurred on a regular basis and be updated to identify new potential threats. Here are a few good primer questions to get you started: A lot of these questions are self-explanatory. This tool is not intended to serve as legal advice or as recommendations based on a provider or professionals specific circumstances. It also determines how they might affect the objectives of an IT project. Insights on cybersecurity and vendor risk management. Risk analysis can help an organization to improve their security in many ways. xb```b`` Without a risk assessment to inform your cybersecurity choices, you could waste time, effort and resources there is, after all, little point implementing measures to defend against events that are unlikely to occur or wont have much material impact on your organization. Learn why security and risk management teams have adopted security ratings in this post. The risk analysis process usually follows these basic steps: The focus of the analysis, as well as the format of the results, will vary depending on the type of risk analysis being carried out. Many breaches come from. Stay up to date with security research and global news about data breaches. How long would it take and what would be the associated costs? Vendor relationship questionnaire moving out of beta.
0000008010 00000 n
This operating system has a known backdoor in version 1.7 of its software that is easily exploitable via physical means and stores information of high value on it. Take a tour of UpGuard to learn more about our features and services. Here's What to Do! Categorizing risks in this way helps organizations and/or project teams decide which risks can be considered low priority and which have to be actively managed to reduce the effect on the enterprise or the project. Book a free, personalized onboarding call with one of our cybersecurity experts. All rights reserved. Sign-up now. Beyond that, cyber risk assessments are integral to information risk management and any organization's wider risk management strategy. Are there financial or legal penalties associated with exposing or losing this information? Control third-party vendor risk and improve your cyber security posture. Copyright 2000 - 2022, TechTarget So, an organization that has done a quantitative risk analysis and is then hit with a data breach should be able to easily determine the financial impact of the incident on its operations. What would be the reputational damage of this, High - corrective measures to be developed as soon as possible, Medium - correct measures developed within a reasonable period of time, Low - decide whether to accept the risk or mitigate, Tolerance for uncertainty regarding risk factors, The organizational weighting of risk factors. 0000002224 00000 n
All information entered into the tool is stored locally on the user's computer. Knowing organizational vulnerabilities gives you a clear idea of where your organization needs to improve. Theft of trade secrets, code, or other key information assets could mean you lose business to competitors. A risk assessment helps your organization ensure it is compliant with HIPAAsadministrative, physical, and technical safeguards. Purchase the lasted ISO/IEC 27005 Standard >>. But don't forget physical vulnerabilities, the chance of someone gaining access to an organization's computing system is reduced by having keycard access. Copyright 2011-2021 www.javatpoint.com. Concerning financial and organizational impacts, it identifies, rate and compares the overall impact of risks related to the organization.  Mail us on [emailprotected], to get more information about given services. This is a complete guide to security ratings and common usecases. To find out more on how our cybersecurity products and services can protect your organization, or to receive some guidance and advice, speak to one of our experts. They will also need to follow a number of steps and create relevant documentation as part of the information security risk treatment process. xref
The international standardISO/IEC 27001:2013(ISO 27001) provides the specifications of a best-practice ISMS (information security management system) a risk-based approach to corporate information security risk management that addresses people, processes and technology. This step is responsible for monitoring the security risk on a regular basis for identifying, treating and managing risks that should be an essential part of any risk analysis process. The SRA Tool is a desktop application that walks users through the security risk assessment process using a simple, wizard-based approach. Cookie Preferences After analysis of the Risk that provides an idea about which assets are valuable and which threats will probably affect the IT assets negatively, we would develop a plan for risk management to produce control recommendations that can be used to mitigate, transfer, accept or avoid the risk. The next step is easy: if it costs more to protect the asset than it's worth, it may not make sense to use preventative control to protect it. Is this the highest priority security risk? Download our free green paper Risk assessment and ISO 27001 to receiverisk assessmenttips from the ISO 27001 experts. It identifies the possible adverse events that could occur in an organization such as human error, flooding, fire, or earthquakes. 5357 0 obj<>stream
0000009783 00000 n
Who do I need access to in the organization to get all the information I need? IT leaders are learning how to implement blockchain, a distributed ledger technology, within their organizations. Ideally, organizations should have dedicated in-house teams processing risk assessments.
Mail us on [emailprotected], to get more information about given services. This is a complete guide to security ratings and common usecases. To find out more on how our cybersecurity products and services can protect your organization, or to receive some guidance and advice, speak to one of our experts. They will also need to follow a number of steps and create relevant documentation as part of the information security risk treatment process. xref
The international standardISO/IEC 27001:2013(ISO 27001) provides the specifications of a best-practice ISMS (information security management system) a risk-based approach to corporate information security risk management that addresses people, processes and technology. This step is responsible for monitoring the security risk on a regular basis for identifying, treating and managing risks that should be an essential part of any risk analysis process. The SRA Tool is a desktop application that walks users through the security risk assessment process using a simple, wizard-based approach. Cookie Preferences After analysis of the Risk that provides an idea about which assets are valuable and which threats will probably affect the IT assets negatively, we would develop a plan for risk management to produce control recommendations that can be used to mitigate, transfer, accept or avoid the risk. The next step is easy: if it costs more to protect the asset than it's worth, it may not make sense to use preventative control to protect it. Is this the highest priority security risk? Download our free green paper Risk assessment and ISO 27001 to receiverisk assessmenttips from the ISO 27001 experts. It identifies the possible adverse events that could occur in an organization such as human error, flooding, fire, or earthquakes. 5357 0 obj<>stream
0000009783 00000 n
Who do I need access to in the organization to get all the information I need? IT leaders are learning how to implement blockchain, a distributed ledger technology, within their organizations. Ideally, organizations should have dedicated in-house teams processing risk assessments.  Before you can do that though, you need to answer the following questions: This will help you understand the information value of the data you are trying to protect and allow you to better understand your information risk management process in the scope of protecting business needs. This process is done in order to help organizations avoid or mitigate those risks. 0000008920 00000 n
Before you can do that though, you need to answer the following questions: This will help you understand the information value of the data you are trying to protect and allow you to better understand your information risk management process in the scope of protecting business needs. This process is done in order to help organizations avoid or mitigate those risks. 0000008920 00000 n
0000010408 00000 n
Quantitative risk analysis helps in calculating estimates of overall project risk which is the main focus. What is the impact if those vulnerabilities are exploited? But should organisations deploying artificial intelligence comply with EU or UK proposals? Protect your sensitive data from breaches. <<85a8539914c51a488feaa5c68cacc9fd>]>>
To learn more about the assessment process and how it benefits your organization,visit theOffice for Civil Rights' official guidance. You can then create a risk assessment policy that defines what your organization must do periodically to monitor its security posture, how risks are addressed and mitigated, and how you will carry out the next risk assessment process. Clause 6.1.2 of the standardsets out the requirements of the information security risk assessment process. 0000001394 00000 n
This will allow you to prioritize which assets to assess. Start my free, unlimited access. Use of this tool is neither required by nor guarantees compliance with federal, state or local laws. The qualitative risk analysis process is a project management technique that prioritizes risk on the project by assigning the probability and impact number. It is a critical component of risk management strategy and data protection efforts. Now it's time to move from what "could" happen to what has a chance of happening. But you expect that this is unlikely to occur, say a one in fifty-year occurrence. Before you start assessing and mitigating risks, you need to understand what data you have, what infrastructure you have, and the value of the data you are trying to protect. Are there any priorities or constraints I should be aware of that could affect the assessment? 0000000958 00000 n
National Institute of Standards and Technology (NIST), cyber attack compromising a particular operating system, monitor their cybersecurity score, prevent breaches, S3 buckets holding sensitive information properly configured, Personally identifiable information (PII), financial and reputational damage to your business and how they are mitigated. Here are some general guidelines: Remember, you have now determined the value of the asset and how much you could spend to protect it.



